Keeping the Costs Low
December 14, 2019
Based on my last post I decided to find a way of limiting TPS rate my site can take. Idea is to invert the traditional way of creating a site or web application and then doing performance tests to validate that it can handle the expected load. In this model you simply decide how much load your site should take and then make it fail when that limit is breached. So instead of improving performance, you limit the costs.
I am not expecting that many visitors to my site so I decided that my site should hanlde 2 TPS. I also decided that I want to have a layer above S3 so that S3 bucket will not be directly visible to Internet. CloudFront can hide my S3 bucket with website content from direct public access and also offers some nice CloudWatch metrics e.g. requests / minute in order to track TPS rate for the site. CloudFront together with S3 and Hugo also gave me some headaches, but I will get back to those in a later post.
It is not exactly easy to calculate possible maximum costs in this scenario as costs will be divided to multiple AWS services. But in order to keep things a bit simpler we can use the pure S3 scenarios from last post with TPS rate of 2:
- 1 GB of Storage
- 5 356 800 GET requests
- Average response size 10 kB
- 51 GB of data transfer out
This would generate ca. $ 7 (plus tax) of costs if site would be constantly under 2 TPS load. I can live with that.
So I started Googling and came across this article: Serverless Automated Cost Controls, Part1. It describes a way of detecting budget breaches and taking actions based on that to limit costs. I wanted to reuse this idea but make it a bit simpler for my use case.
The solution
I made a private S3 bucket where I put my content. Then I added that into CloudFront distribution as REST endpoint, so that I can disable access to my site simply by disabling this CloudFront distribution. CloudWatch keeps track of traffic flowing to my site and is able to create alarms when there are more than 120 request / minute (2 TPS). This alarm will then go to SNS and Lambda function will pick it up from there and disable CloudFront distribution.
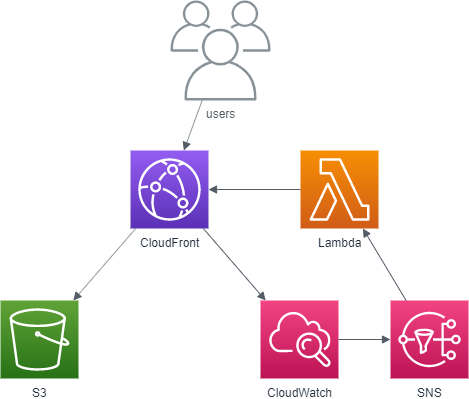
Alarm will also be sent to my email as I have added my email as subscriber in SNS. CloudFront distribution will remain disabled until I enable in manually again. While it is disabled, there will be no costs to my AWS account as my content is not reachable from public Internet.